EmpowerID Account Store Definitions Configuration
Overview
This document provides comprehensive guidance on defining and managing account stores within EmpowerID. It is tailored for experienced Identity Access Management (IAM) professionals who require an in-depth understanding of each configurable setting, its purpose, and its relationship to other IAM processes. This narrative will provide the necessary context to implement robust and optimized account store configurations.
Understanding Account Stores in EmpowerID
Account stores are integral to EmpowerID’s architecture, representing external systems such as Active Directory, AWS, Google Apps, or SCIM-based systems. These connections enable EmpowerID to inventory, synchronize, and manage identities while extending capabilities like authentication and provisioning.
Key Concepts:
- Accounts vs. Person Objects: Accounts are external identities retrieved from integrated systems. These are distinct from "person objects," which are managed identity representations within EmpowerID. This distinction is critical, as person objects serve as the central entities for RBAC and other IAM processes.
- System Types: EmpowerID supports various predefined system types, each with unique characteristics and configuration needs, such as cloud gateways for remote systems or secure binding options for directories like Active Directory. For each of the various system types, the configuration page and corresponding tabs may differ based on the requirements of the specific account store system type.
Creating a new Account Store Definition
There are some common basic steps for creating and configuring a new account store definition in EmpowerID. Depending on the system type of the account store (Active Directory, EntraID, SAP, LDAP, SuccessFactors, etc.), the specific details will vary but the basic process will be fairly consistent.
Step 1 - Run the Create Account Store Workflow
- Navigate to the Admin --> Applications and Directories -->Account Stores and Systems page
- Select the Account Stores tab
- Click on the Create Account Store workflow in the right hand menu pane.
Step 2 - Select the system type
- search for the system type for the account store you want to create
Step 3 - Enter the basic metadata for the account store
- Enter basic name and description information so you can find the account store in the list once created
Step 4 - Enter the Required System Connectivity Information
Depending on the system type you are connecting to, this information will vary
- For Active Directory, you will enter the FQDN of the domain, the Proxy Account username and password, and the Netbios domain name
- For SAP S4/Hanna, you will need the ServerType, Host, Proxy Account username and password, System Number, and Client
- For Linux you will need the Server Name, Proxy Account Username and Password, or optionally, the Certificate file and password
- For other systems, you can find the requirements in the EmpowerID online documentation at docs.empowerid.com
Step 5 - Select the Cloud Gateway
For remote systems that are not local to the EmpowerID instance, such as on-premise systems in an EmpowerID SaaS implementation, you will need to search for and select a Cloud Gateway server that resides in an environment local to the target system.
Step 6 - Configure the Remaining Account Store Settings
Save the basic system definition and then bring up and edit the newly created account store to continue configuring the operational system settings that define the identity and processes required for the account store. These system settings are discussed in the following sections.
For purposes of this topic, we will use the configuration screens specific to an Active Directory Account Store definition.
Configurable Settings: A Detailed Exploration
Account Store Configuration Page Tabs
The Account Store Definitions page is divided into separate tabs which separate the major areas of configuration. The following sections detail the configuration options under each area.

General Tab
The General Tab provides the foundational configuration for the account store. It includes fields for basic settings such as the account store name, type, IT environment designation (e.g., production, development, or testing), and connectivity settings. This tab also contains security configurations like proxy account settings, vaulted credentials, and secure binding options. Additionally, visibility in EmpowerID’s IAM Shop and fallback paths for account and group creation are defined here. The purpose of this tab is to establish the identity and security framework for the account store.

Account Store Name
The Account Store Name is a unique identifier for the account store within EmpowerID. This name is used in administrative interfaces and logs to easily identify the connection. It should be descriptive enough to indicate the purpose or system associated with the account store.
IT Environment Type
The IT Environment Type field categorizes the account store by its deployment context, such as Development, Testing, Staging, or Production. This classification helps administrators understand the purpose and operational stage of the account store, enabling better organization and monitoring within large environments.
Account Store Type
The Account Store Type allows for further categorization of the account store. Examples include IT Directory Services, HR Systems, Finance Systems, and more. This field is primarily for administrative organization and does not directly impact functionality.
Specify a Proxy Account
The Proxy Account is the set of credentials EmpowerID uses to authenticate and interact with the external system. For example, in an Active Directory environment, the proxy account must have sufficient permissions to read directory objects, synchronize data, and perform any required administrative tasks.
Select a Vaulted Credential
The Vaulted Credential option leverages EmpowerID’s privileged access management capabilities. This feature securely stores and retrieves the proxy account credentials, reducing the need to manually enter sensitive information during configuration. Vaulted credentials enhance security and compliance.
Use Secure LDAPS Binding
The Use Secure LDAPS Binding setting determines whether EmpowerID uses Secure LDAP (LDAPS) to communicate with directory services. Enabling this ensures encrypted communication, enhancing security when transmitting sensitive data such as authentication credentials.
Inventoried Directory Server
The Inventoried Directory Server field specifies the primary directory server used for inventory processes. EmpowerID communicates with this server to retrieve data such as user accounts, groups, and organizational units. The selection of the appropriate server can optimize synchronization and inventory efficiency.
Is Remote (Cloud Gateway Required)
The Is Remote setting indicates whether the account store is located outside the local network and requires the EmpowerID Cloud Gateway for connectivity. This gateway acts as a secure intermediary, enabling connections to remote systems while maintaining data integrity and security.
Is Visible in IAM Shop
The Is Visible in IAM Shop setting determines whether resources from the account store, such as user accounts and groups, are available for requests through the EmpowerID self-service portal. Enabling this setting allows users to request access or manage resources tied to the account store directly through the portal.
Authentication and Password Settings for Account Store Definitions

Use for Authentication
The Use for Authentication field determines whether EmpowerID can utilize accounts from the specified account store as an authentication source. Enabling this option allows EmpowerID to validate login credentials against this account store. For example, Active Directory accounts can be used to authenticate users accessing the EmpowerID system. This is particularly useful when Active Directory serves as an Identity Provider (IdP).
Allow Search for Username in Authentication
The Allow Search for Username in Authentication setting enables EmpowerID to search across all account stores flagged for authentication when a user logs in. This eliminates the need for users to prepend a domain or specific identifier to their username, streamlining the login process. For instance, instead of entering DOMAIN\username, a user can simply enter username if this setting is enabled.
Allow Password Sync
The Allow Password Sync field enables automatic synchronization of password changes between EmpowerID and the account store. When a user's password is updated in EmpowerID, the change is propagated to the linked account in the account store. This setting ensures consistency in credential management across integrated systems and is crucial for environments requiring unified password policies.
Queue Password Changes
The Queue Password Changes option provides resilience in scenarios where connectivity with the account store is unreliable. If a password change attempt fails due to a network or system issue, the request is queued and retried until successful. This ensures that password updates are eventually synchronized, maintaining system integrity even in challenging network environments.
Password Manager Policy for Accounts without Person
The Password Manager Policy for Accounts without Person setting applies password policies to accounts in the account store that are not joined to a person object in EmpowerID. These accounts, often referred to as orphaned accounts, include service accounts, training accounts, or administrative accounts. This field ensures that even unlinked accounts adhere to appropriate password management policies, enhancing security and compliance.
Provisioning Settings for Account Store Definitions
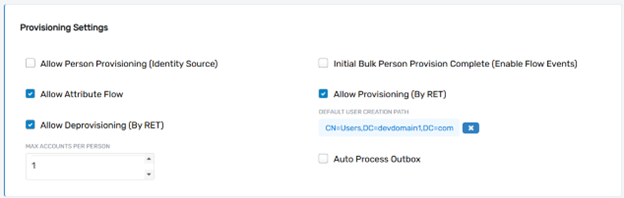
Allow Person Provisioning (Identity Source)
The Allow Person Provisioning field determines whether accounts from the selected account store can be used as a source for creating managed person objects in EmpowerID. This is often enabled for authoritative systems, such as HR platforms, where new employee records should automatically trigger the creation of corresponding person objects in EmpowerID. For non-authoritative systems like Active Directory, this setting is typically disabled to avoid duplicate person objects.
Initial Bulk Person Provision Complete (Enable Flow Events)
The Initial Bulk Person Provision Complete field activates flow events when new accounts are detected in the account store. These events are processed through EmpowerID’s no-code workflows, allowing administrators to automate actions such as assigning roles, sending notifications, or linking the accounts to existing person objects.
Allow Attribute Flow
The Allow Attribute Flow setting enables synchronization of attributes between the accounts in the account store and their corresponding person objects in EmpowerID. This ensures that key information, such as email addresses, job titles, or department details, remains consistent across the integrated systems. Disabling this setting halts attribute updates for the linked accounts and person objects.
Allow Provisioning (by RET)
The Allow Provisioning by Resource Entitlements (RET) field enables EmpowerID’s automated provisioning policies to create new accounts in the account store. For instance, a user assigned to a specific role might automatically have an account created in a connected system like Active Directory. Disabling this prevents automated account creation, requiring manual provisioning instead.
Allow Deprovisioning (by RET)
The Allow Deprovisioning by Resource Entitlements (RET) field allows automated policies to deprovision accounts in the account store when they are no longer required. For example, if a user’s role is removed, their associated accounts can be disabled or deleted according to the deprovisioning rules. Disabling this prevents automated account removal, ensuring that account deletion is a manual process.
Default User Creation Path
The Default User Creation Path specifies the Organizational Unit (OU) or container in the external system where new user accounts will be created if no explicit path is provided during the provisioning process. This fallback path ensures that provisioning requests succeed even when the target location is undefined.
Max Accounts Per Person
The Max Accounts Per Person field defines the maximum number of accounts in the account store that can be linked to a single person object in EmpowerID. Typically set to 1 to maintain a one-to-one relationship, this can be increased in scenarios where a person requires multiple accounts for administrative or functional purposes.
Business Role Settings for Account Store Definitions
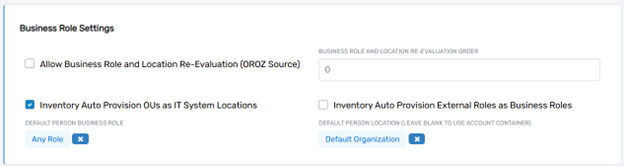
Allow Business Role and Location Re-Evaluation (OROZ Source)
The Allow Business Role and Location Re-Evaluation field enables EmpowerID to derive business role and location assignments for person objects from the account store. If enabled, data such as organizational unit (OU) or job title from the account store can be used to update or assign roles and locations within EmpowerID. This is particularly useful for HR systems or other authoritative sources that maintain organizational hierarchies or role data.
Business Role and Location Re-Evaluation Order
The Business Role and Location Re-Evaluation Order determines the priority of the account store when multiple systems provide conflicting business role and location data. Systems with higher priority take precedence in assigning these attributes to person objects. This setting is crucial in environments with multiple authoritative sources for identity data.
Inventory Auto-Provision OUs as IT-System Locations
The Inventory Auto-Provision OUs as IT-System Locations field governs whether organizational units (OUs) inventoried from the account store are automatically created as IT-system locations in EmpowerID. This feature helps administrators manage and assign permissions to locations based on the external system’s structure, ensuring consistency between the directory and EmpowerID.
Inventory Auto-Provision External Roles as Business Roles
The Inventory Auto-Provision External Roles as Business Roles setting allows EmpowerID to automatically create internal business roles from external roles inventoried in the account store. For instance, roles defined in an HR system can be translated into EmpowerID business roles, streamlining the integration process and ensuring consistent role management.
Default Person Business Role
The Default Person Business Role specifies the business role assigned to a person object when no explicit role information is available from the account store. This fallback ensures that newly created person objects have at least a baseline role assignment for access and management purposes.
Default Person Location
The Default Person Location defines the default physical or organizational location assigned to a person object when no location information is available from the account store. This setting helps maintain a complete identity profile even when data is incomplete or unavailable.
Group Settings for Account Store Definitions

Allow Account Creation on Membership Request
The Allow Account Creation on Membership Request field enables EmpowerID to automatically create user accounts in the account store when a person is assigned to a group within that store. For this to function, specific workflows must be active in EmpowerID, such as those that handle account provisioning based on group membership. This feature is particularly useful in scenarios where group membership dictates access to external systems, ensuring accounts are created as needed.
Recertify External Group Membership Additions as Detected
The Recertify External Group Membership Additions as Detected field activates real-time recertification for new group memberships detected in the account store. When EmpowerID inventories group memberships from the external system and detects additions, it triggers a recertification process. This process involves sending the membership change for approval to the group owner or another designated approver, ensuring that all group memberships are verified and compliant with access policies.
SetGroup of Groups to Monitor for Real-time Recertification
The SetGroup of Groups to Monitor for Real-time Recertification field allows administrators to specify a subset of groups to be included in the recertification process. This is particularly important in environments with thousands of groups, where it may not be practical or necessary to recertify every group membership change. By defining a target set of groups, organizations can focus recertification efforts on high-risk or high-priority groups.
Default Group Creation Path
The Default Group Creation Path specifies the organizational unit (OU) or container within the account store where new groups are created if no explicit path is provided. This fallback path ensures that group creation requests succeed even when the target location is undefined, maintaining operational continuity in automated workflows.
EmpowerID Group Creation Path
The EmpowerID Group Creation Path is used by EmpowerID’s backend processes for creating system groups, such as dynamic groups or enforcement groups. For instance, when EmpowerID generates groups to enforce permissions for file shares or other resources, those groups are placed in the specified path. This setting ensures that system-generated groups are organized and easily identifiable within the account store.
Directory Cleanup Settings for Account Store Definitions
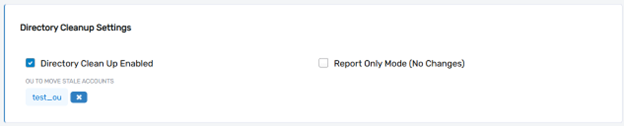
Directory Cleanup Enabled
The Directory Cleanup Enabled field activates the directory cleanup process for the account store. This process identifies stale accounts—accounts that have not been active for a defined period—and applies actions based on configuration settings. Enabling this feature ensures that outdated or unused accounts are managed effectively, improving overall directory hygiene and security.
Report Only Mode (No Changes)
The Report Only Mode (No Changes) setting configures the directory cleanup process to generate reports without making any actual changes. This is useful for auditing purposes, allowing administrators to review the accounts identified as stale and validate the cleanup criteria before enabling actions such as moving or deleting accounts.
OU to Move Stale Accounts
The OU to Move Stale Accounts field specifies the organizational unit (OU) or container within the account store where stale accounts should be relocated. Instead of deleting inactive accounts, they are moved to this designated location, providing a safer alternative for organizations that prefer to retain accounts for historical or compliance purposes while removing them from active directories.
Special Use Settings for Account Store Definitions
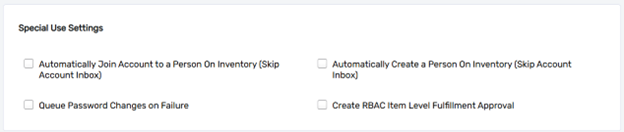
Automatically Join Account to a Person on Inventory (Skip Account Inbox)
The Automatically Join Account to a Person on Inventory field enables EmpowerID to automatically associate inventoried accounts with existing person objects without processing them through the Account Inbox. This is particularly useful in sandbox or testing environments where account-person relationships need to be established quickly without applying standard evaluation criteria or workflows.
Automatically Create a Person on Inventory (Skip Account Inbox)
The Automatically Create a Person on Inventory setting allows EmpowerID to bypass the Account Inbox and automatically create person objects for all inventoried accounts. This setting is typically used in non-production environments where the immediate creation of person objects is necessary, regardless of evaluation criteria or filters. It streamlines processes in scenarios where every inventoried account must have a corresponding person object.
Queue Password Changes on Failure
The Queue Password Changes on Failure field provides resiliency in password management. If a password change attempt fails—for example, due to temporary connectivity issues with the account store—this setting ensures the failed change request is added to a queue. The queued request is retried until the update is successfully applied, maintaining consistency across systems and minimizing the risk of unsynchronized credentials.
Inventory Tab
The Inventory Tab manages the synchronization of data between the account store and EmpowerID. It allows administrators to enable or disable The inventory process and schedule inventory intervals. The inventory process is critical for maintaining data consistency and ensuring real-time updates to account-related changes.
This process can be scheduled with granularity ranging from continuous inventory (every 10 minutes) to periodic updates (daily or weekly). The schedule must align with system update frequencies to ensure near real-time data consistency.
Membership Tab
The Membership Tab focuses on group membership reconciliation within the account store. It allows for the configuration of membership inventory schedules and enables the detection and synchronization of changes in group memberships. This tab ensures that EmpowerID accurately reflects group memberships from the external system, enabling the system to enforce access controls and manage entitlements effectively.
This process can be scheduled with granularity ranging from continuous inventory (every 10 minutes) to periodic updates (daily or weekly). The schedule must align with system update frequencies to ensure near real-time data consistency.
Projection Tab
The Projection Tab is used for specialized scenarios where EmpowerID creates external resources, such as groups, to enforce permissions or manage access. For example, it might be used to create Active Directory groups for file share permissions or other hierarchical structures. This tab is typically not utilized in standard configurations but becomes essential in environments requiring automated resource creation and projection based on predefined policies.
Deleted Items Detection Tab
The Deleted Items Detection Tab provides settings for identifying and managing objects that have been removed from the external system. In systems like Active Directory, this tab is not needed since EmpowerID can scan the Deleted Items Container (Recycle Bin) to know what objects have been deleted. For systems without such features, EmpowerID can perform a full comparison during inventory to identify discrepancies. This tab ensures that EmpowerID’s identity warehouse remains in sync with the external system by flagging or removing stale objects.
Extension Tab
The Extension Tab allows administrators to add descriptive metadata to the account store definition that can be used for further categorization or labeling of the account store. These fields are often used programatically to provide a workflow or process with supplemental metadata regarding the account store.
Conclusion
This document has detailed the majority of standard configurable settings for EmpowerID account stores, providing an exhaustive reference for IAM professionals. By understanding the purpose and interconnectivity of these settings, administrators can tailor configurations to align with organizational requirements, ensuring a secure and efficient identity management system.