Overview of EmpowerID RBAC Architecture
Introduction
Role-Based Access Control (RBAC) in EmpowerID offers a structured approach for defining policy and assigning access within the system. It serves two primary purposes:
-
Persona Definitions: These definitions control what a user sees and can do within the EmpowerID UI when performing tasks or maintenance activities. When users log into EmpowerID, their available functionalities and environment depend entirely on their assigned RBAC permissions.
-
Birthright Access: This defines the external system access automatically assigned to users based on their job role or department. Birthright access includes provisioning of accounts, access to required applications, and membership in essential groups to ensure users can perform their job functions effectively.
Delegation Model
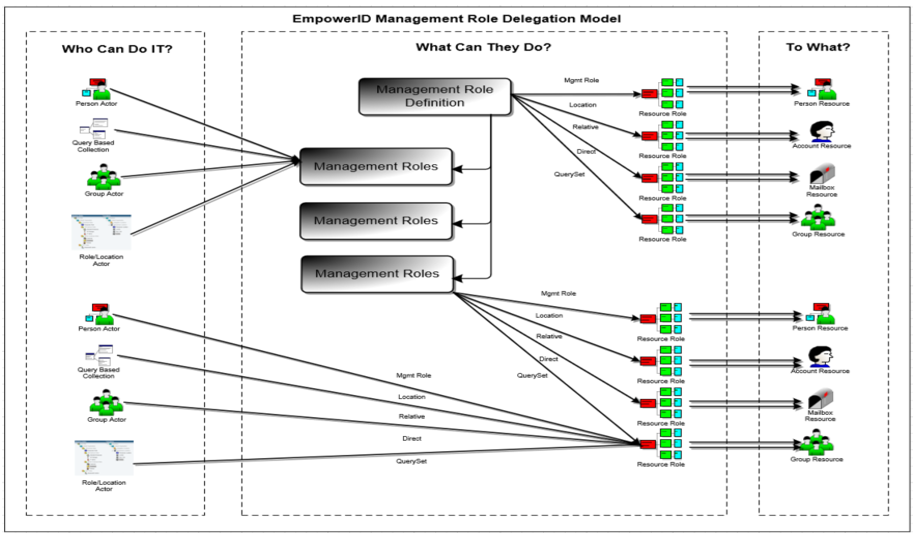
Delegation within EmpowerID is fundamental to RBAC management, structured around answering three essential questions:
- Who can do it? (Actors or Assignee Types)
- What can they do?
- To what resources can they do it?
EmpowerID addresses "who can perform actions?" through RBAC actors, also known as assignee types. These actors represent distinct points from which permissions can be granted or inherited within EmpowerID’s delegation model. The concept of inheritance is crucial—actors can acquire permissions either directly or indirectly based on their associations or memberships.
EmpowerID defines the following RBAC actors (assignee types):
-
Groups: Permissions assigned to groups are automatically inherited by their members, simplifying permission management through group memberships.
-
Management Roles: Management roles bundle multiple access levels together, creating permission sets across resources and systems. Members assigned to a management role inherit all permissions within that role. These roles can be independently managed, with owners controlling assignments, performing membership recertifications, and administering cross-system access flexibly.
-
Business Roles and Business Locations: These roles reflect HR-driven organizational positions and physical or logical locations. EmpowerID assigns permissions at this combined role and location level, which individuals then inherit. This structure enables efficient and automated delegation of access as employees move between roles or locations, dramatically reducing complexity and administrative overhead.
-
Query-Based Collections: These are dynamic groups defined by SQL queries, which automatically update their membership based on the specified criteria within EmpowerID. Permissions granted to query-based collections are inherited by all individuals matching the query criteria, facilitating automated, adaptive permission delegation as organizational attributes change.
-
Persons: Individuals are the primary RBAC actors since they directly interact with the EmpowerID user interface to perform actual tasks. They inherit permissions assigned to any of the other actor types, whether from groups, management roles, business roles, business locations, or query-based collections.
This detailed framework clearly addresses three core delegation questions:
- Who can perform actions? (Actors)
- What actions or operations can they perform? (Granular permissions like creating accounts, deleting users, resetting passwords, or managing groups.)
- Upon what resources or scopes can they execute those permissions?
Together, these foundational elements form the comprehensive delegation model that allows EmpowerID to maintain precise, scalable, and secure control over organizational access.
Major RBAC Components
The major components that form EmpowerID's RBAC infrastructure include Operations, Access Levels, Management Roles, and Business Roles and Locations. Understanding each component’s role and interactions is essential for effectively leveraging EmpowerID’s RBAC capabilities.
Operations
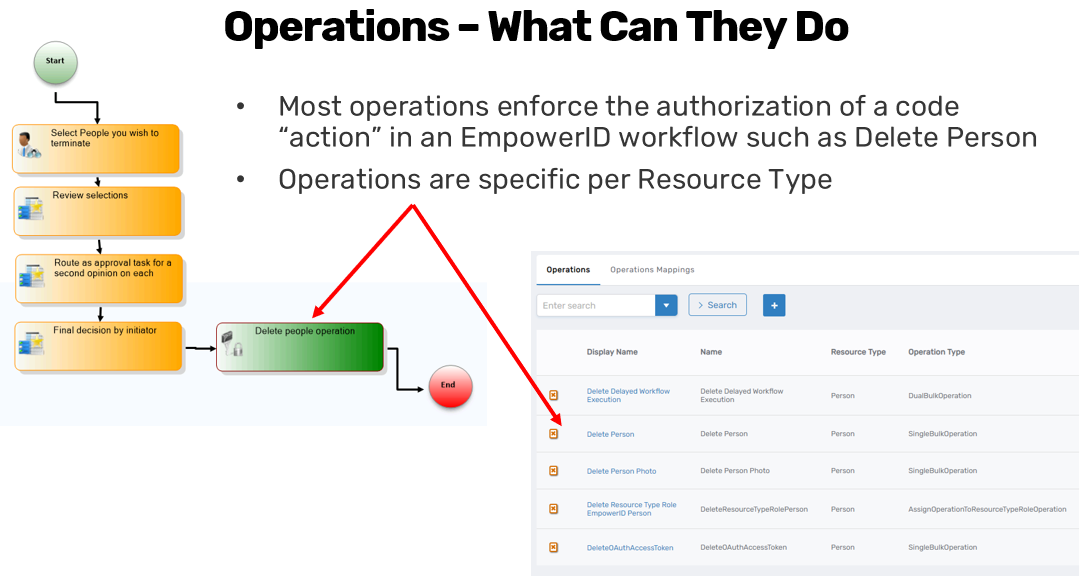
Operations represent the most granular actions users can perform within EmpowerID workflows. Each operation corresponds to a specific action executed against a particular resource type, such as deleting a person, resetting an account password, or managing group memberships. EmpowerID maintains thousands of operations, each tied explicitly to a resource type—like accounts, persons, groups, or roles.
For example, operations such as "Delete Person," "Unlock Account," and "Reset Account Password" explicitly define the actions that can be authorized within EmpowerID. However, these granular operations are not directly assigned to individual users or actors. Instead, they must first be packaged into groups called "Access Levels."
Access Levels
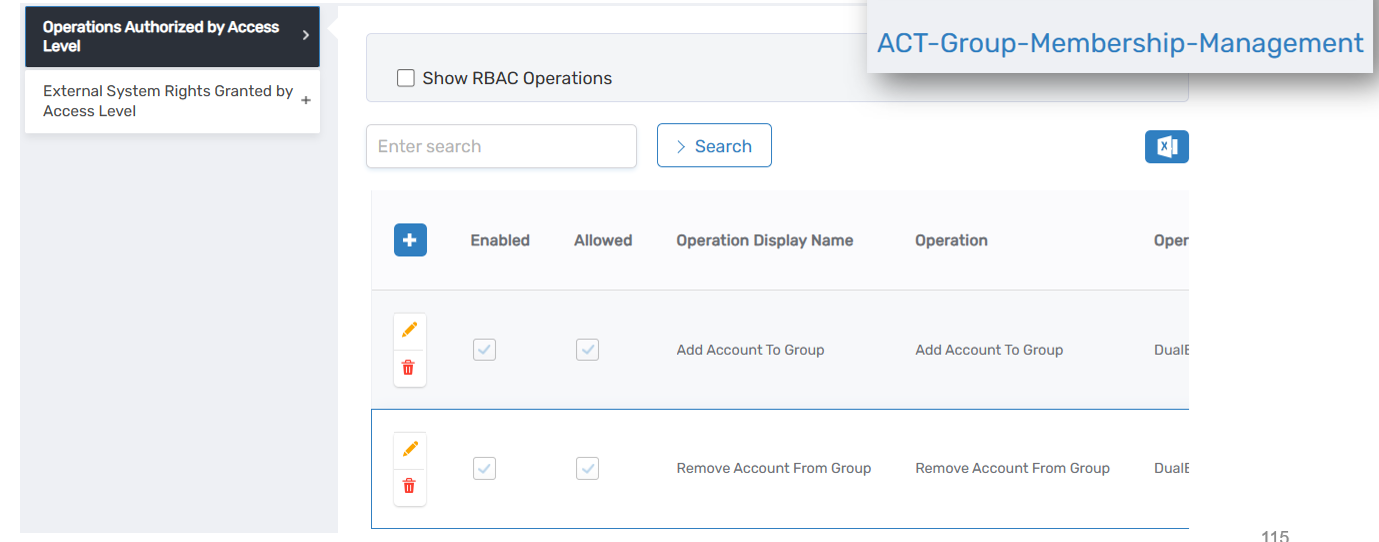
Access Levels, also known within EmpowerID as "Resource Roles," bundle related operations into manageable units based on resource type. They simplify delegation by allowing multiple operations to be assigned collectively, reducing complexity and administrative overhead.
Each Access Level is tied explicitly to a particular resource type and scope. For example, an Access Level called "Account Password Help Desk" might bundle operations essential for help desk personnel, such as "unlock account," "reset account password," and "set password options." Administrators then assign these Access Levels to specific resource scopes—for example, allowing help desk personnel to manage accounts within certain departments or divisions. This bundling mechanism ensures streamlined permission management while clearly defining the boundaries of what users can do against defined sets of resources.
Management Roles
Management Roles are higher-level bundles consisting of multiple Access Levels, effectively creating cross-system access packages. They enable EmpowerID administrators to assign extensive permission sets across various resources and systems in a simplified, modular manner.
Unlike Access Levels, Management Roles are typically not tied directly to HR assignments. This independence offers flexibility, allowing organizations to create functional roles that are not strictly bound by job descriptions or departments. Management Roles are typically governed by designated owners who can manage role memberships, handle assignments, approve requests, and conduct recertification of roles to ensure permissions remain accurate over time. They can also be requested through EmpowerID’s IAM Shop interface, allowing users or their managers to initiate requests for access as needed.
Additionally, EmpowerID provides special Management Roles known as "Task-based RBAC (T-RBAC)" roles, specifically designed as foundational building blocks for creating persona-based user experiences. These roles bundle management roles together to provide users with the precise functionality they require within EmpowerID.
Business Roles and Business Locations
Business Roles and Business Locations form EmpowerID’s core organizational framework. They directly reflect the organizational structure provided by HR systems, defining "what a user does" (Business Role) and "where they perform it" (Business Location).
A Business Role describes an organizational job title or function, such as analyst, sales representative, department manager, or director. A Business Location describes a physical, geographical, logical, or operational location, such as departments, divisions, offices, regions, or virtual structures like projects.
EmpowerID uses these roles and locations in combination, which allows administrators to assign permissions efficiently while significantly reducing redundancy and complexity—known as "role bloat." Instead of needing separate roles for each unique location-job combination, EmpowerID leverages a polyarchical structure that separates role definitions from location contexts. Permissions assigned at higher levels (for example, at a divisional or organizational-unit level) automatically inherit downward, cascading permissions to all associated lower-level roles or locations.
For instance, assigning permissions at the "Finance Division" level would automatically grant those permissions to all users assigned to departments or locations within the Finance Division. EmpowerID aligns its internal Business Locations with external system structures, such as Active Directory Organizational Units (OUs), to synchronize and simplify cross-system management and integration. This alignment allows consistent, centralized control of permissions both within EmpowerID and across external identity systems, ensuring a seamless and unified identity and access management strategy.
Collectively, these components—Operations, Access Levels, Management Roles, and Business Roles and Locations—form the comprehensive RBAC infrastructure in EmpowerID, ensuring secure, scalable, and easily maintainable access management aligned with organizational structure and operational needs.
Polyarchical Business Role Structure, Assignments, and Delegation Model
EmpowerID employs a sophisticated polyarchical business role structure designed specifically to manage complex identity and access requirements effectively. Traditional RBAC frameworks often experience role explosion—also known as "role bloat"—where managing individual roles for every unique combination of job function and location becomes excessively cumbersome. For example, if an organization operates globally, a traditional flat RBAC model might necessitate hundreds of nearly identical roles, such as "Bank Teller - New York," "Bank Teller - Tokyo," and "Bank Teller - London," each with slightly different permissions tailored to the local environment. Managing and visualizing such an enormous number of roles becomes extremely challenging, both administratively and from a self-service perspective.
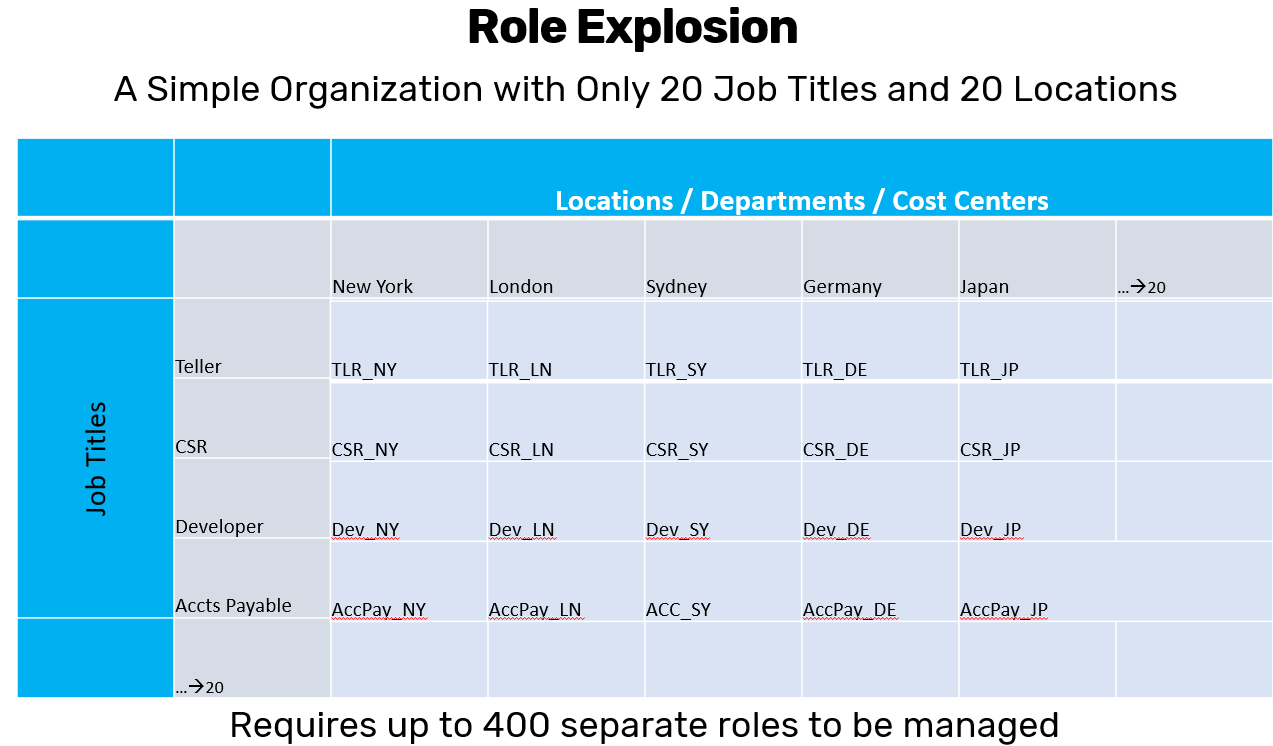
EmpowerID's innovative polyarchical approach addresses these challenges by clearly distinguishing and managing two separate but interconnected hierarchies: Business Roles and Business Locations.
Business Roles and Locations
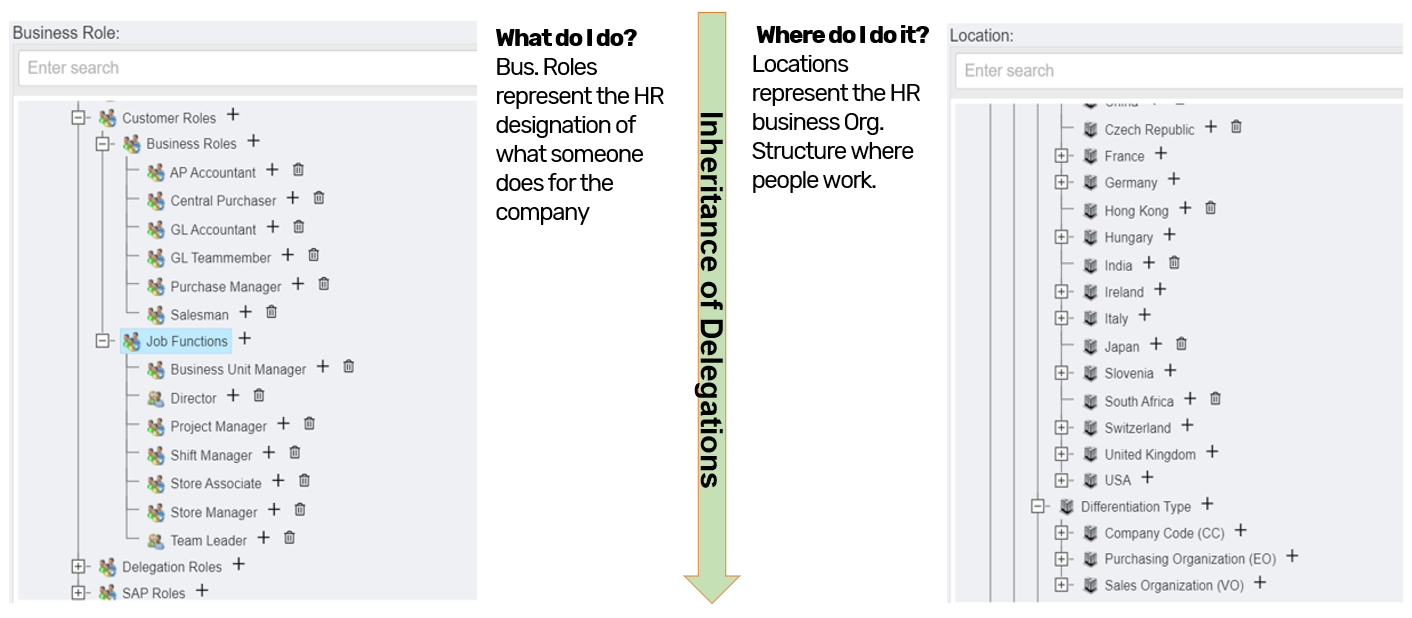
Business Roles represent the organizational functions or positions provided by HR systems. These are functional titles or responsibilities, such as Analyst, Project Manager, Sales Representative, or Department Director. The Business Role defines "what a person does" within an organization, independent of their specific location or departmental placement.
Business Locations, on the other hand, define the organizational, geographical, operational, or logical contexts within which these roles operate. These contexts may be represented as divisions, departments, geographical regions, or even virtual or project-based groupings.
By separating "what you do" (role) from "where you do it" (location), EmpowerID creates a dynamic, flexible inheritance structure that significantly reduces role complexity. Permissions assigned at higher levels within either the business role or location hierarchy automatically cascade downwards, inheriting to lower-level roles or locations. For instance, if administrators assign a set of permissions to the "Finance Division" business location, all sub-departments and teams within that division automatically inherit these permissions, eliminating the need to manage permissions individually at each lower-level location.
Similarly, permissions assigned to higher-level business roles cascade downward. Assigning specific permissions or group memberships to a top-level role, such as "Customer Roles," ensures every role nested below it—such as customer service representatives, support analysts, or sales associates—automatically inherits these permissions.
Role and Location Assignments
In EmpowerID, each user's identity is explicitly linked to both a Business Role and a Business Location simultaneously. This dual assignment provides a clear and comprehensive context for defining the user’s identity, responsibilities, and required access permissions. For example, rather than assigning a user simply as an "Analyst," EmpowerID requires assignment to both "Analyst" (the role) and a specific department, like "Engineering" or "Sales," defining precisely where the user performs their function. This approach ensures precise, contextualized permission management aligned closely with HR records and organizational structure.
The combined business role and location assignment dynamically governs a user's permissions and access. As individuals move between roles or departments within the organization—tracked through HR-driven data—EmpowerID automatically updates their role-location assignments. Consequently, users instantly gain or lose inherited permissions and birthright access, reflecting their current position and responsibilities without manual intervention.
Delegation and Inheritance Model
EmpowerID’s delegation model enhances this polyarchical structure by clearly defining how permissions and resource visibility flow throughout the hierarchy. Delegation and permission assignments inherently cascade downward, meaning permissions assigned at higher-level business roles or locations automatically propagate down to lower-level roles or locations. For instance, assigning permission at the "Corporate Headquarters" business location grants permissions to all subordinate offices or departments beneath it.
Conversely, resource visibility flows upward within the hierarchy. Resources and user identities assigned at lower levels within the location hierarchy become visible at higher levels. For example, a user assigned to the "Brussels" location would be visible when administrators view resources from the higher-level "Belgium," "Europe," or "All Business Locations" nodes. This upward visibility simplifies administration and oversight, providing clear, hierarchical views of user identities and associated permissions across the entire organizational structure.
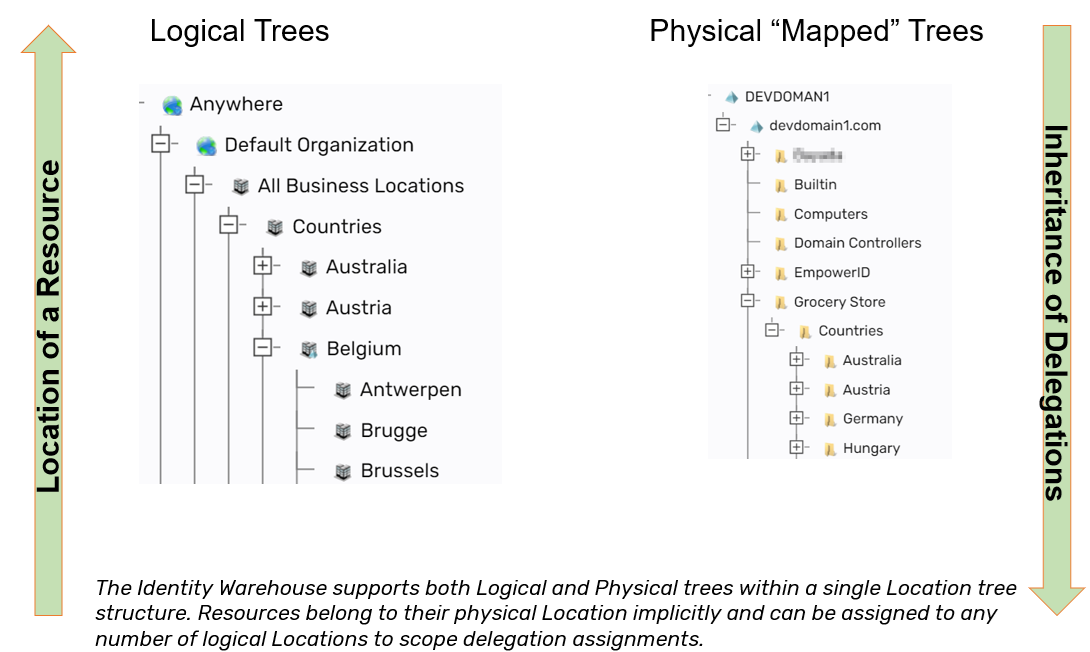
EmpowerID aligns its internal Business Locations with external system structures, such as Active Directory Organizational Units (OUs), to synchronize and simplify cross-system management and integration. This alignment allows consistent, centralized control of permissions both within EmpowerID and across external identity systems, ensuring a seamless and unified identity and access management strategy.
Collectively, these capabilities—polyarchical role-location inheritance, dynamic and contextualized role-location assignments, and clear delegation and visibility models—offer EmpowerID users a highly scalable, efficient, and manageable identity and access management framework. This robust structure significantly reduces complexity, eliminates redundant administrative tasks, and ensures precise, secure permissions that dynamically reflect organizational needs and structures.